Losing Your Biggest Customer To An Unsolicited Security Review Is Not Fun
When your largest customer decides to audit your security without warning, you learn quickly whether your "secure coding practices" are actually enough.
Reality Check: Customers are assessing your app security behind your back
StayTuned builds and acquires ecommerce applications used by thousands of ecommerce merchants. With $34 million in funding and a portfolio of high-traffic apps, they were exactly the kind of company that should have security figured out.
Their engineering team followed best practices. Clean code, regular QA, modern development workflows. Like most fast-growing SaaS companies, they thought this was adequate.
Then their largest customer and integration partner — initiated an unsolicited security review as part of their supply chain risk management program.
The review flagged multiple security issues across StayTuned's applications. The message was clear:
"These vulnerabilities need to be resolved, or we'll need to reconsider our partnership. "
For StayTuned (like most B2B SaaS businesses), losing their biggest customer wasn't just about losing a customer. It would have been catastrophic.
StayTuned Snapshot
✔ Company: StayTuned Apps
✔ Industry: Ecommerce
✔ Funding: $34 million Series A
✔ Customers: Over 20,000
✔ Tech: Shifted left to run security from its CICD pipelines without slowing down new feature development speed
✔ Developers: >500
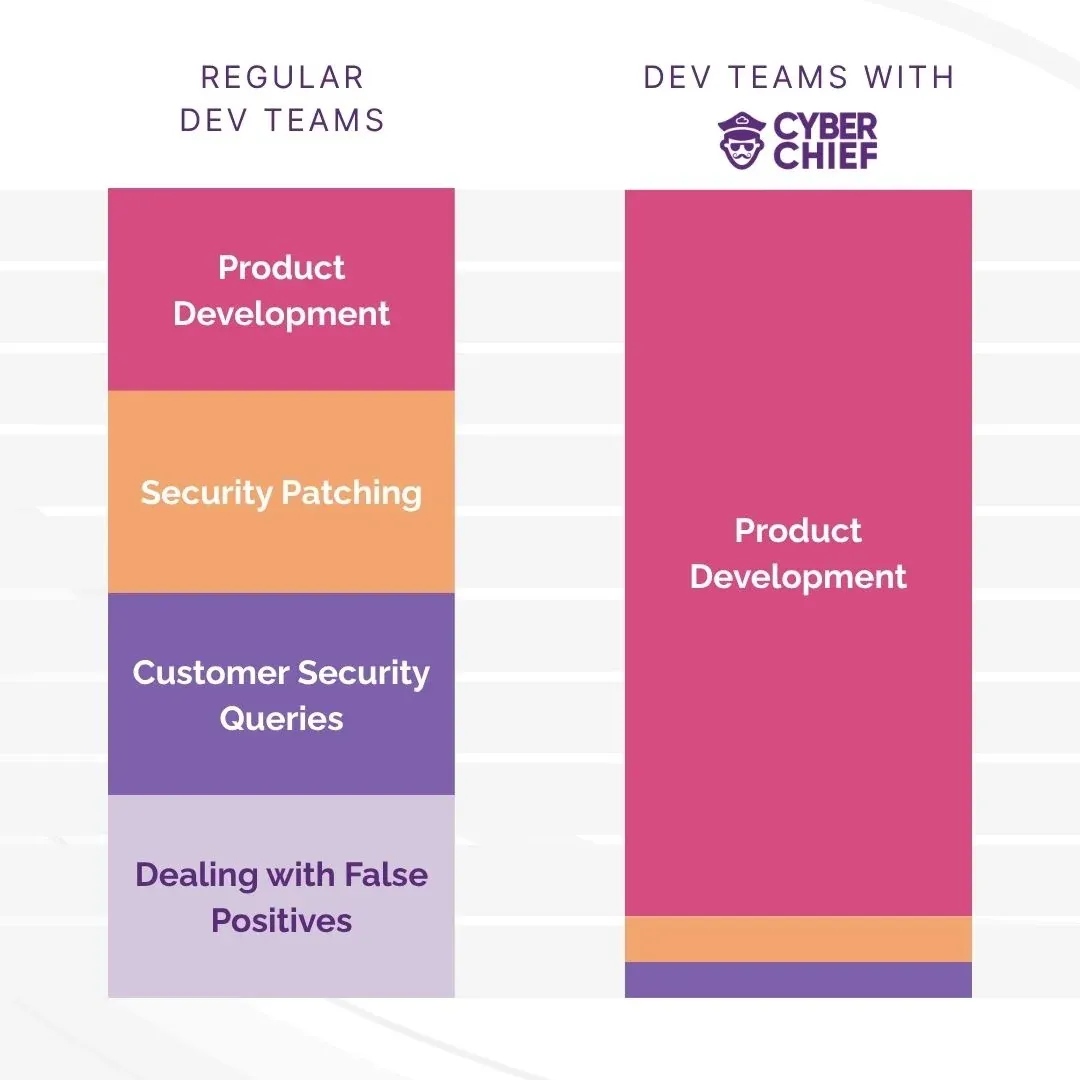
The truth? There's a big gap between "secure coding" & "secure apps"
From the outside, it's surprising: a well-funded company; an experienced dev team. So why do these issues even exist?
Because like many fast-scaling SaaS companies, StayTuned’s focus was on shipping product, not building an internal security team.
They had used open-source scanners and believed they used secure coding practices, but that was not enough.
Their challenge wasn't technical incompetence. The hidden vulnerabilities weren't simple, missing HTTP headers.
They were critical issues borne from unfamiliar, inherited code, the kind that leads to customers leaving in droves when exploited.
StayTuned needed to resolve the immediate findings, but more importantly, they needed a way to prevent future surprises.
We weren't looking for a checkbox exercise. We wanted to understand what was actually wrong and how to fix it without derailing our development speed.
AppSec that works with dev, not against it
Even though our QA team doesn't specialize in security, they could replicate and validate every finding because the documentation was that clear.
StayTuned turned to Audacix and Cyber Chief to deliver more than a report. They needed a repeatable process that did not require building a security team.
The engagement began with a manual penetration test tailored to their complex modern web app.
But instead of generating another PDF report, Each finding came with clear risk context, reproducible steps and fixes their devs implemented immediately:
Issues tracked in Jira with detailed remediation guidance
Clear priority rankings based on actual business risk
Developer-ready fixes that didn't require security expertise to implement
Direct Slack support for questions during remediation
Randy didn't stop there. He wanted to embed security visibility into their workflows.
The real value: control over your security timeline
StayTuned switched on 5 key Cyber Chief capabilities to automate security tests from their CI/CD pipelines.
No vague summaries. No back-and-forth. Just clear, actionable insight their team could move on immediately.
Despite not having a dedicated security team, StayTuned’s QA engineers were able to replicate and validate every finding with confidence.





The automation setup was intuitive and fast. It fits into our workflows without adding overhead.
AppSec without slowing down or hiring expensive experts
What made the difference for StayTuned wasn’t just the scan results. It was the cultural shift.
Security moved from firefighting to a function their development team owned.
Their engineering team can now:
Address security proactively at the source, rather than reactively
Plan security work around new feature release priorities
Fix issues with confidence using developer-friendly guidance
Prove security posture to customers and partners on demand
And there's no need to hire a security department, or consign the dev team to weeks of chaos every time a pentest report lands.
I’ve seen the extremes of everything being manual or everything being software. Both don’t give me enough confidence. You guys are definitely in the proper category.
Knowing your biggest customer won't find security issues before you do is the best sleeping pill
This wasn't just about passing a security review. It was about taking control of security before external pressures force reactive decisions.
Top SaaS engineering leaders like Randy, chase 4 powerful outcomes:
X-ray vision - see what’s actually fragile in your stack before your customer, your auditor, or your CEO asks.
A kill switch - something that says “fix this now” and means it. Not a red circle buried on slide 47.
Steering power - so security doesn’t stall your next release, hijack sprint planning, or trigger a game of “Who’s owning this?”
Show receipts - the kind that prove you're not winging security when a prospect drops a procurement questionnaire that reads like a CSI episode.
Because here’s the thing no one tells you - you don’t need more findings, just more control & fewer surprises.
⭐⭐⭐⭐⭐They have excellent catches for vulnerabilities on our platform, but what is more important they are always available to discuss potential fixes, taking into account our business requirements.