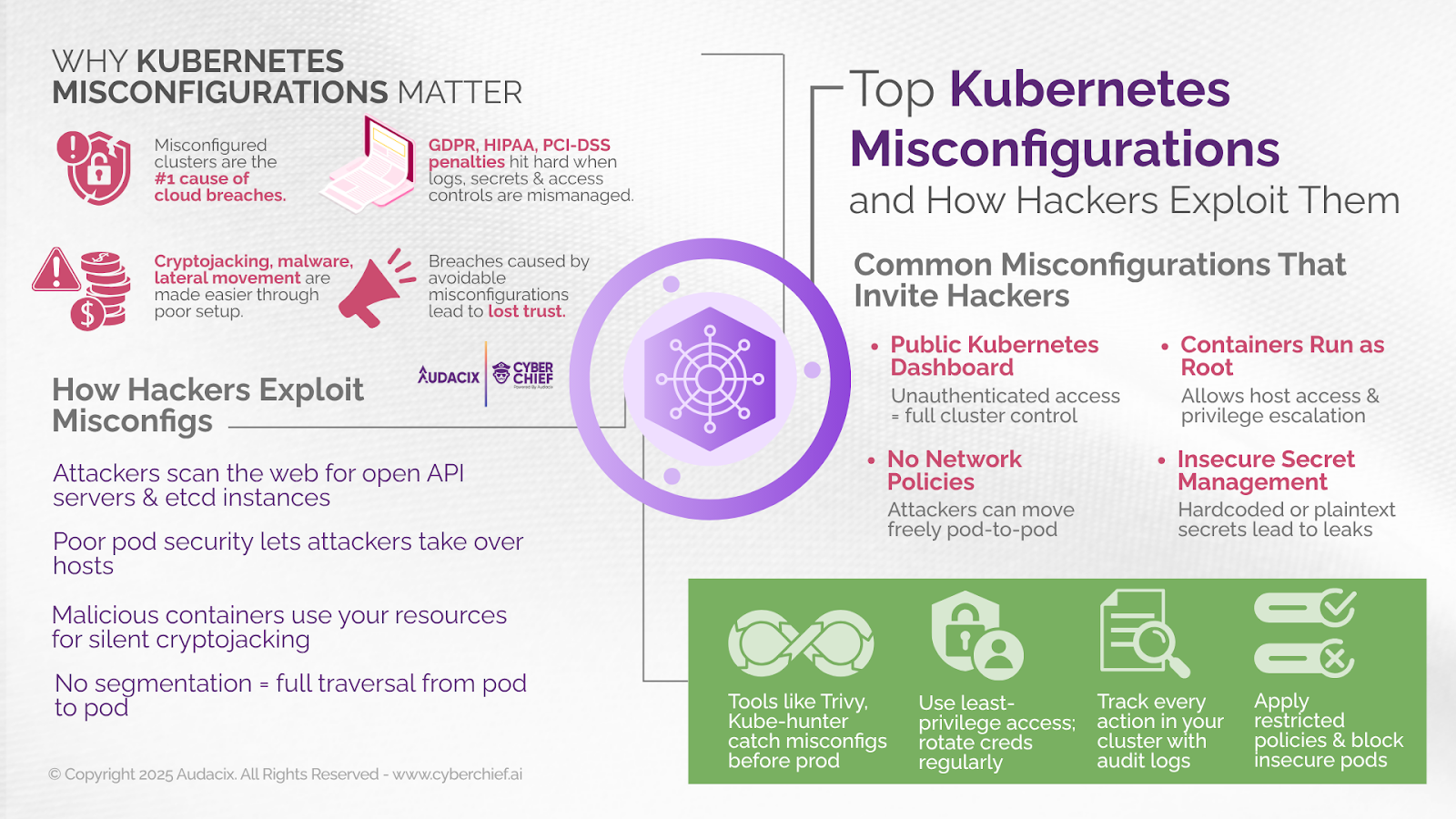
If you're working with Kubernetes, it's important to understand what misconfiguration is and why it matters. A misconfiguration happens when Kubernetes components or resources are set up in a way that’s insecure or incorrect, usually by mistake. These aren’t bugs in Kubernetes itself but rather issues that come from how it's used. For example, you might accidentally expose the Kubernetes API server or dashboard to the public, which can allow unauthorized access. Running containers as root is another common issue that gives attackers more control if they get in. Granting users or services too many permissions through RBAC (Role-Based Access Control), not restricting pod-to-pod communication, and leaving the etcd database unprotected are other risky mistakes. These kinds of misconfigurations can open the door to serious security threats, so it’s crucial to configure your Kubernetes environment carefully and review it regularly.
Why Misconfigurations Matters
1. They Create Security Vulnerabilities
Misconfigurations in Kubernetes clusters significantly increase your attack surface and expose critical security vulnerabilities. For instance, improperly exposing the Kubernetes API server to the internet without third-party authentication providers or multi-factor authentication can allow attackers to gain access and compromise your entire cluster. According to leading reports from Gartner and Palo Alto Networks, such misconfigurations are the primary cause of cloud security incidents. Failing to implement security best practices like limiting service account tokens, setting proper pod security context, and hardening control plane components opens doors to privilege escalation and unauthorized access. Strengthening your Kubernetes infrastructure security through proactive security measures is essential to protect your workloads and sensitive data, minimizing security risks .
2. They Lead to Compliance Violations
If your Kubernetes environment processes regulated or sensitive data, compliance with frameworks like GDPR, HIPAA, and PCI-DSS requires enforcing stringent security controls and access control settings. Storing Kubernetes secrets insecurely, failing to use transport layer security for secure communication, or neglecting to enable audit logging are common misconfigurations that violate compliance standards. Poor handling of security context settings, resource usage, and access control can result in fines, audits, and legal repercussions. Ensuring proper role-based access control (RBAC), implementing strong access controls using a restricted pod security standard, and controlling network access via Kubernetes network policies are foundational security requirements to meet regulatory obligations.
3. They Open the Door to Cryptojacking and Malware
Attackers frequently exploit weak security mechanisms in Kubernetes to inject malicious containers or container images that execute cryptojacking scripts or malware. A real-world example is Tesla’s breach, where an unsecured Kubernetes dashboard led to attackers mining cryptocurrency within their Kubernetes infrastructure. Without controlling network traffic, setting strict firewall rules, or monitoring active network traffic, your cloud resources can be hijacked silently. Poorly configured container runtime, service accounts, and lack of privilege escalation controls amplify the security threats. Hardening your security posture with Kubernetes security best practices, like restricting root user access and regularly rotating infrastructure credentials, is key to preventing such exploits.
4. They Impact Business Reputation
A Kubernetes control plane breach due to poor infrastructure security or mismanaged security policies can lead to public security incidents and downtime. This loss of trust impacts your brand, customers, and stakeholders. Failing to secure external services, Kubernetes API endpoints, or properly control system calls can result in the compromise of customer data, leading to reputational damage that’s difficult to recover from.
5. They Increase Operational Costs
Every misconfiguration adds layers of hidden cost. From increased resource usage due to rogue containers, to emergency patching and forensics, the expenses mount quickly. Lack of proper security context and pod security admission settings can cause widespread impact, forcing teams to audit and reconfigure the Kubernetes infrastructure. Teams may also need to invest in commercial security solutions and expand monitoring to control network traffic and monitor network traffic, leading to higher operational overhead.
6. They Slow Down Development
A poorly configured Kubernetes deployment, especially regarding the container runtime, can break CI/CD pipelines, hinder secure communication, and block developers from deploying updates efficiently. Misconfigured access control settings, missing security considerations, and improperly enforced network policies can delay releases, reduce system visibility, and cause developer frustration. Adopting strong security controls, using Linux security modules, and limiting resource usage can improve stability and boost productivity.
Ten Most Common Security Misconfigurations in Kubernetes & How to Mitigate Them
Here are the 10 most common security misconfigurations we’ve seen, and exactly how you can fix them to protect your Kubernetes infrastructure:
1. Exposing the Kubernetes Dashboard Without Authentication
What’s the risk?
Leaving the dashboard publicly accessible or skipping authentication gives anyone the ability to control your entire cluster, a massive security threat.
What you should do:
Enable Role-Based Access Control (RBAC) to limit who can access the dashboard.
Block external network access unless absolutely necessary.
Use multi-factor authentication with a third-party provider for dashboard access.
2. No Role-Based Access Control (RBAC)
What’s the risk?
Granting users (or service accounts) cluster-admin by default opens the door to privilege escalation and exposes your control plane.
What you should do:
Define fine-grained RBAC policies - avoid blanket permissions.
Assign the least privilege needed for the task.
Periodically audit permissions and rotate infrastructure credentials.
3. Running Containers as Root
What’s the risk?
Running containers as the root user gives attackers a pathway to escape the container and compromise your host operating system.
What you should do:
Set runAsNonRoot: true in the pod security context.
Drop unnecessary capabilities and control system calls via Linux Security Modules (AppArmor, SELinux).
Avoid using base images that run as root by default.
4. Not Using Network Policies
What’s the risk?
By default, all pods can talk to each other, which makes lateral movement easy in the event of a breach.
What you should do:
Define NetworkPolicies to control network traffic between pods.
Separate workloads by namespace and apply network segmentation.
Actively monitor network traffic for anomalies.
5. Publicly Exposed etcd
What’s the risk?
etcd is the source of truth for Kubernetes, holding all secrets and cluster configurations. If someone gains access, it’s game over.
What you should do:
Enable TLS and client certs for secure etcd communication.
Lock down access using firewall rules and IP whitelisting.
Ensure only the API servers can reach etcd.
6. Poor Secret Management
What’s the risk?
Storing secrets in plaintext or in version control puts sensitive data at serious risk.
What you should do:
Use Kubernetes Secrets (encrypted at rest).
Integrate with external secret managers (e.g., AWS Secrets Manager, HashiCorp Vault).
Avoid long-lived service account tokens, rotate credentials regularly.
7. Insecure API Server Config
What’s the risk?
A misconfigured Kubernetes API server can be an easy entry point for attackers.
What you should do:
Enforce authentication, authorization, and access control.
Restrict API server access with firewall rules and IP allowlists.
Enable audit logging for visibility and incident tracking.
Always use Transport Layer Security (TLS).
8. Allowing Privileged Containers
What’s the risk?
Setting privileged: true effectively removes sandboxing, allowing full host access, loading unwanted kernel modules, and more.
What you should do:
Ban privileged containers unless absolutely necessary.
Use Pod Security Admission and adopt the restricted pod security standard.
Scan your container images for embedded privileges or insecure defaults.
9. No Pod Security Policies or Admission Controls
What’s the risk?
Without policy enforcement, pods can run with insecure configurations or escalate privileges.
What you should do:
Implement PodSecurityAdmission with strict baseline or restricted policies.
Use Kyverno, OPA/Gatekeeper, or other security policy controllers.
Limit resource usage and control what images can run where.
10. Unrestricted Ingress Traffic
What’s the risk?
Leaving Ingress wide open can expose internal services to the public internet — a big attack surface.
What you should do:
Use Ingress controllers that support TLS, secure headers, and rate limiting.
Apply firewall rules and IP-based access controls.
Consider using a Web Application Firewall (WAF) for sensitive apps.
| Misconfiguration | Risk | Fix |
|---|---|---|
| Dashboard opens to the internet | Full cluster access | Restrict with auth, VPN |
| No RBAC | Over-permissioned users | Use fine-grained RBAC |
| Containers run as root | Host takeover | Use non-root user, set runAsNonRoot |
| No network policies | Lateral movement | Define strict NetworkPolicies |
| etcd exposed | Secret leaks | Lock down etcd access, enable TLS |
| Secrets in Git | Credential theft | Use external secret managers |
| No PodSecurityPolicies | Dangerous pod specs | Use OPA/Kyverno or PodSecurity admission |
| Privileged containers | Host access | Avoid privileged mode |
| API server wide open | Remote takeover | Use authN/authZ and audit logging |
| Ingress open to all | Service exposure | Use firewalls, limit CIDRs |
How Hackers Exploit Cloud Misconfigurations
Misconfigured Kubernetes clusters significantly increase the attack surface, and attackers often rely on automated tools to identify and exploit security vulnerabilities. Strengthening your Kubernetes security posture requires understanding these common security incidents:
1. Exposed Services & Control Plane Components
Poorly secured Kubernetes control plane components like the API server, etcd, and dashboards—especially when lacking transport layer security or third-party authentication providers—can allow unauthorized network access. Attackers actively monitor network traffic to find open ports or misconfigured external services that lack secure communication protocols.
Best Practice: Restrict network traffic, enforce firewall rules, and limit network access to only the API servers through proper network policies and access control settings.
2. Container Escapes & Privilege Escalation
Containers running with an insecure pod security context or privileged access pose critical security risks. If containers run as the root user, attackers can exploit weak security context settings or Linux Security Modules to escape the container runtime and compromise the operating system.
Best Practice: Use the restricted pod security standard, limit system calls, and configure pod security admission and security context parameters properly.
3. Cryptojacking & Resource Abuse
After initial access, attackers frequently deploy malicious container images to engage in cryptojacking, exploiting resource usage across the entire cluster without immediate detection. The lack of limiting resource usage allows them to monetize your infrastructure.
Best Practice: Set security policies and quotas to limit Kubernetes deployments' resource usage and monitor for spikes in active network traffic or CPU activity.
4. Data Theft via Kubernetes API
Unauthorized access to Kubernetes secrets, service account tokens, or the Kubernetes API server itself can lead to exposure of sensitive data, environment variables, and configurations. Attackers often exploit misconfigured role-based access control (RBAC) or unprotected control plane components.
Best Practice: Apply strong access control policies, rotate infrastructure credentials frequently, and avoid granting cluster admin access unless necessary.
5. Lateral Movement Across the Cluster
Without proper Kubernetes network policies or security mechanisms Kubernetes offers, attackers can traverse from one pod or namespace to another, compromising additional parts of the Kubernetes infrastructure.
Best Practice: Implement network security policies to control network traffic between workloads and avoid overly permissive service accounts.
6. Persistence Mechanisms
Threat actors may create malicious init containers, backdoors, or alter ConfigMaps to persist in the Kubernetes environment. They may also load unwanted kernel modules or manipulate the security context of future pods.
Best Practice: Enable audit logging, use commercial security solutions, and regularly audit for abnormal behaviors and security threats.
Best Practices to Prevent Misconfigurations
Enable Audit Logging to Track API Server Activity and Detect Security Incidents
One of the foundational Kubernetes security best practices is to enable audit logging on the Kubernetes API server. Audit logs record every interaction with the API server—what actions were taken, when, and by whom. These logs help detect unauthorized access attempts, misconfigurations, and other security incidents. Think of it as a surveillance system for your Kubernetes control plane. For optimal infrastructure security, integrate audit logs with a commercial security solution or a SIEM system to analyze anomalies and track security threats in real-time. This visibility is crucial for strengthening your security posture and ensuring that you can respond swiftly to incidents targeting your Kubernetes infrastructure.
Regularly Scan Kubernetes Clusters for Vulnerabilities and Misconfigurations
To harden your Kubernetes environment, regularly scan your Kubernetes clusters using tools like Cyber Chief Raider. Cyber Chief Raider can detect security vulnerabilities in control plane components, container images, and Kubernetes deployments, and assess compliance with security policies. Scans reveal flaws such as privilege escalation, insecure service account tokens, or weak security context settings. Integrate these scans into your CI/CD pipeline to proactively address security risks before deployment. This minimizes your attack surface and enhances Kubernetes infrastructure security.
Use Infrastructure as Code with Built-in Security Controls and Automated Checks
Managing your Kubernetes infrastructure via Infrastructure as Code (IaC) tools like Terraform and Helm ensures consistent and auditable deployments. However, IaC code can introduce security concerns if left unchecked. Use Cyber Chief Raider CSPM to scan IaC for security best practices, such as avoiding granting cluster admin access, securing service accounts, and implementing restricted pod security standards.
Keep Kubernetes and Related Components Up to Date
Patching and upgrading Kubernetes control plane components and the container runtime is essential to close off known security vulnerabilities. Outdated components, including kubelet, kubectl, and kube-proxy, increase your exposure to security threats. Set a regular update schedule and use automation tools like Kured to handle reboots after patching. Keeping up with the latest versions helps prevent attackers from exploiting outdated security mechanisms Kubernetes relies on, and is a vital part of maintaining a resilient security posture.
Continuously Monitor Configurations with Cloud Security Posture Management Tools
In dynamic cloud-native environments, misconfigurations can emerge quickly. Cloud Security Posture Management (CSPM) tools help by continuously monitoring your Kubernetes environment for violations of security requirements, such as controlling access to sensitive data, limiting resource usage, and enforcing pod security admission. CSPM tools identify and alert on access control issues, misused network policies, overly broad firewall rules, and exposed external services. This constant vigilance helps enforce network security, improves infrastructure security, and protects your entire cluster from inadvertent exposure.
Implement Strong Network Security and Access Controls
Effective network security in Kubernetes involves setting up network policies to control network traffic between pods and services. This helps prevent unauthorized attempts to gain access to internal resources. Monitor active network traffic and enforce firewall rules to restrict network access to only the API servers or required endpoints. Use transport layer security (TLS) for secure communication, and configure third-party authentication providers with multi-factor authentication (MFA) to prevent unauthorized service account use. Also, enforce role-based access control (RBAC) and avoid granting cluster admin access unnecessarily.
Harden Security Contexts and Limit Privileges
Define strong pod security context and security context settings to prevent privilege escalation, loading unwanted kernel modules, and unsafe system calls. Disable running containers as the root user, and apply Linux security modules such as AppArmor or SELinux. Apply restricted pod security standards and use pod security admission to enforce policies across the entire cluster. These security measures drastically reduce the risk of containers breaking isolation or escalating privileges within the cluster.
Protect Sensitive Data and Rotate Credentials Frequently
Secure Kubernetes Secrets, certificates, and infrastructure credentials using encryption and access controls. Avoid embedding sensitive data directly into configuration files. Implement automatic credential rotation and enforce strict access control around secrets. These steps protect your Kubernetes infrastructure from leaks or misuse due to human error or attacks targeting static secrets.
By combining these security controls, monitoring practices, and tools, you can build a robust Kubernetes security strategy that safeguards your Kubernetes infrastructure from both internal and external security threats. Implementing these security best practices ensures your Kubernetes environment remains secure, resilient, and compliant.
Why You Need a DevSecOps Culture for Kubernetes (and How to Do It Right)
If you’re managing applications on Kubernetes and not thinking about security every step of the way, you’re putting your systems, and your users at risk. Kubernetes is powerful, but with that power comes complexity and a growing attack surface. That’s where DevSecOps comes in: the practice of integrating development, security, and operations into a single, collaborative workflow.
Let’s break this down so it’s not just theoretical, but practical — something you can start applying right now.
1. Build a DevSecOps Culture That Fits Kubernetes
Traditional security practices don’t work in a fast-moving Kubernetes world. You can’t "scan at the end" and hope for the best. In a DevSecOps culture, security becomes part of everyone’s job — developers, DevOps engineers, platform teams, and security analysts.
Why does this matter? Because Kubernetes is built for scale and speed, and if security isn’t integrated from the beginning, vulnerabilities slip through.
What you should do:
Involve security teams early in your Kubernetes adoption or migration.
Create cross-functional teams where security specialists support developers and ops, not block them.
Shift from security as a gate to security as a guide — empowering teams to make safe choices on their own.
2. Make Security Part of Your CI/CD Pipeline
You can’t secure Kubernetes if your CI/CD pipelines are pushing broken or insecure code. By integrating security tools into your build and deploy processes, you catch issues before they hit production — when they’re cheaper and easier to fix.
Kubernetes thrives on automation. Your CI/CD pipeline must enforce security controls from the start:
Scan every container image for vulnerabilities before deployment. Use tools that detect outdated libraries, malware, or exposed secrets.
Run automated checks for misconfigurations — for example, images running as the root user, or excessive resource usage.
Validate security context settings. Enforce policies that prevent containers from having unnecessary write access, privilege escalation, or hostPath volumes that expose the node.
Adopt Pod Security Admission with the restricted pod security standard, ensuring that workloads comply with Kubernetes security best practices by default.
All these security mechanisms help ensure you’re not pushing security issues into your Kubernetes infrastructure
3. Train Developers and Operators — Constantly
You can buy the best security tools in the world, but if your team doesn’t know how to use them — or doesn’t even know what risks to look out for, you’re still vulnerable. People are your strongest (or weakest) link.
What this looks like in action:
Run training sessions tailored to Kubernetes. Developers should understand things like container image vulnerabilities, using minimal base images, and how privilege escalation can occur in pods.
Train operators on security best practices such as setting up Role-Based Access Control (RBAC), managing secrets securely (not hardcoding them in YAML!), and using network policies.
Encourage a culture of secure defaults. Developers should know that exposing a service with LoadBalancer or using hostPath mounts can open big holes in your cluster.
This is not a “one and done” task. Make training a part of onboarding and regular team development.
4. Enforce Policies and Run Regular Security Audits
Kubernetes gives you flexibility — sometimes too much. A single misconfigured pod or overly permissive RBAC role can compromise your entire cluster. That’s why regular audits and policy enforcement are non-negotiable.
What this means:
Use tools like Cyber Chief to enforce security policies around container image origins, network access, service account tokens, and more.
Implement network policies to control network traffic between pods tightly. Without this, any compromised pod could potentially gain access to others, or worse, escalate to control plane components.
Monitor traffic and logs, especially to and from the Kubernetes API server. This is the brain of your cluster; only the API servers should talk to the control plane.
Enable audit logging to trace suspicious activity and detect signs of security threats early.
Security should never be based on trust or luck — enforce it through automation and validation.
Watch the Cyber Chief on-demand demo to see not only how it can help to keep attackers out, but also to see how you can secure your Kubernetes clusters and IaC
How? Cyber Chief not only helps you find vulnerabilities across all components of your application, API and cloud stack. Most importantly, it also helps you fix these vulnerabilities in minutes, not days.
Cyber Chief has been built to integrate with the workflows of high-growth SaaS teams and that's why it offers:
Results from scanning your application for the presence of OWASP Top 10 + SANS CWE 25 + thousands of other vulnerabilities.
A detailed description of the vulnerabilities found.
A risk level for each vulnerability, so you know which ones to fix first.
Best-practice fixes for each vulnerability, including code snippets where relevant.
On-Demand Security Coaching from our application security experts to help you patch vulnerabilities in hours, not days.
Click the green button below to see how Cyber Chief works.